Gang stalking is stalking by several people
who know each other
and who have the same intent.
Mobbing
is the most familiar type of gang stalking.
Bullying
is also a familiar type of gang stalking
when several children participate.
1 in 70 people experience gang stalking.
1 in 30 workers experience mobbing at work.
7 in 10 middle school and high school students
experience bullying in school.
Gang stalking occurs frequently in
apartment buildings,
housing estates,
shops,
and
libraries.
Gang stalking is also perpetrated by
agents of the state,
the
Mafia,
religious sects,
and
utility companies
(electricity, gas, water, telephone, cable TV, internet).
Gang stalking can be so bad
that you can never escape some degree of harassment.
The harassment is often carried out
in a way to blame the victim
for the harassment.
This is called
victim blaming.
Gang stalking by
agents of the state
is an extreme form of fascism.
In particular,
a few victims have proven that they have implants.
This is the most invasive type of stalking.
It’s the most totalitarian invention in history.
Every article about gang stalking on Wikipedia
has been deleted.
Wikipedia has a problem with telling the truth
when it’s embarrassing,
like telling
how many pets are abandoned each year
(about 1 cat and 1 dog per 300 citizens),
not to mention the number of people
who fell under communism,
50 million perhaps?
We urge you to suspend your belief in Wikipedia.
Wikipedia finds pleasure in labeling the victims as mentally ill.
We know that
gang stalking and electronic harassment are designed
to be used against everyone.
At least one Al Qaeda suspect
reported gross human rights violations
in a detention centre in Guantanamo
including electronic harassment.
After a consultation with James Walbert,
Clinical Psychologist Cathy Meadows, M.A. wrote:
“The techniques used against these targeted individuals are purposely designed to make the victim appear to have a mentally disorder in order to invalidate any claims of wrongdoing by the perpetrators. It is a highly organized and multi–faceted attack that is used by many political and religious extremists, by corporations and businesses, and even by organized crime.”

Dr. Seth Farber received his doctorate in psychology in 1984.
www.SethHFarber.com
Dr. Seth Farber wrote:
“Directed energy weapons are among the high-tech arms of the century. They hurt and kill with electromagnetic power. Microwave weapons can be aimed at computers, electrical devices, and persons. They have strong physical and psychological effects and can be used for military and terrorist activities. These weapons are also part of crimes (in Europe) that almost nobody knows except the victims and the offenders. Until now they make the perfect crime possible. No doubt, these weapons have a terrible future.”
If you are a victim,
then I recommend that you download the
backup of my gang stalking websites on May 12, 2014
(ZIP, 209.2 MB).
Save this to a USB stick
and keep it always in your wallet.
This will help you
whenever you have to defend yourself
against accusations of mental illness.
Our definition allows to see different types of gang stalking:
-
mobbing,
-
bullying,
-
stalking in apartment buildings,
-
neighborhood stalking,
-
judges and lawyers who are stalked by the Mafia
because they sent a Mafia member to jail,
-
stalking by the state.
Victims who complain
on the internet
are usually victims of gang stalking by the state.
This is a life long experience.
It’s very difficult to get the word out about this
because:
-
The government denies that this is happening.
-
The police are instructed not to help victims.
-
Doctors are instructed to declare victims crazy.
-
The press refuses to write about it
because they get their tips from the police.
-
The attacks are carried out in a deniable way.
-
There are not many aware victims.
-
The victims are unorganized.
-
The victims have often problems
with employment, housing, justice and so on,
problems caused by perps.
-
The victims can’t say
who would want to do this and why.
-
The victims are often incapacitated
by electronic weapons.
-
Perps pose as victims
and spread ludicrous stories.
They give victims
a bad reputation.
-
No one has ever admitted
that he was a gang stalker.
It can be compared to the time
when no one had ever admitted
that he was a Mafia member.
Specifically we would like to know:
-
Do gang stalkers carry concealed guns?
-
Do gang stalkers have combat training or martial arts training?
-
Do gang stalkers have preparedness training?
-
Do gang stalkers have meetings
where they sing sinister songs?
-
Do gang stalkers have to give
a part of their income
to the stalking organization?
-
Do gang stalkers have to sign blank papers?
-
Do gang stalkers have to agree
with an arranged marriage or adoption?
-
Do gang stalkers have to
‘volunteer’ for medical experiments?
-
Do gang stalkers have to donate organs
to the stalking organization?
Gang stalking
is mentioned in several scientific articles,
which were published in scientific journals.
Gang stalking
was discussed
during a congress for criminologists in Barcelona
in 2008.
The Belgian diplomat
Myrianne Coen
(pronounce Koon)
used to work in the Belgian embassy in Bulgaria.
In 1995 she noticed that
the Belgian Ministry of Foreign Affairs
delivered visas to people
of which she knew
that they were personalities
of the Bulgarian Mafia.
She warned the Ministry several times.
But, they ignored her.
Even worse,
they started to
gang stalk
her.
Finally, in December 1996,
she filed an official complaint
for documents trafficking.
In this complaint,
she describes the gang stalking.
Three months later
she was found unconscious
in the embassy.
The Ministry sent her to a mental hospital.
The diagnosis corroborated the testimony of persons
who were involved in the harassment.
She got fired.
Her career spiralled down.
They tried to cover it up
for several years.
In 2004 the Standing Intelligence Agencies Review Committee
confirmed her claims.
The Bulgarian Mafia had paid for the visas.
She got a new job as an expert
in the Military Centre for Strategic Studies
in Rome.
This affair got much coverage in the news.
In 2006 the Belgian criminologist
Jean-Nicolas Desurmont
interviewed the secret services of Belgium and France,
and 13 victims: a professor, a judge, a lawyer, a diplomat and so on.
Then he published his first article.
His articles are in French.
See
eBooks.
Download
the English translation
(PDF, 724 K, 150 pages, readability 30%, reading age 21).
There are three types of stalking:
-
single stalking,
-
multiple stalking,
-
organizational stalking.
If someone has a divorce
because he wants a gay lifestyle,
and his ex stalks him,
and his neighbor stalks him
because he doesn’t want a gay neighbor,
then this is for the victim
an experience which is different
from the other types,
so we see three types.
Stalking is organizational if:
-
there are at least 2 stalkers,
-
they know each other,
-
they have the same intent.
Organizational stalking is called
gang stalking.
The essence of intimidation in group is:
-
the tyrannical attitude
(denial of the point of view of the defense of the victim),
-
the attitude of denunciation
(circulation of rumors concerning the victim).
There are two types of gang stalking:
-
political gang stalking
perpetrated by
political networks
(government agents),
-
apolitical gang stalking
perpetrated by
apolitical networks
(Mafia).
Apolitical gang stalking
is organized by the Mafia.
Their goal is revenge.
(The Mafia can’t stand
some specific judges and lawyers.)
Political gang stalking
is organized by the
military intelligence.
The goal is to fight organized crime.
Specifically:
to fight apolitical gang stalking
perpetrated by apolitical networks
from other countries.
This is
counterintelligence
so this is done by the army.
Political gang stalking is the usual way
in which large drugs trafficking rings
are dismantled.
The procedure:
-
They choose almost randomly a person.
-
They isolate him
from the people that he knew
by making him appear crazy.
-
He gathers new suspect people around him.
-
All these people are put under investigation.
-
Wherever the suspect people go,
the army recruits snitches.
They form a large network
that collects information.
This can be stimulated
with quota and bonuses
for writing reports.
-
Where it goes from here depends on
the circumstances:
-
Normally it goes on forever.
-
If the suspect people
cause a financial loss for the government,
especially when there’s much drug related crime,
then they are quickly arrested.
-
If the suspect people
appear to be
an apolitical network
then they are dismantled
by monitoring and analyzing
their cell phone use:
the army knows where they are
when they call each other.
In this way
they dismantled a gang stalking network
in Louvain-la-Neuve
(which counts 10,000 citizens)
in Belgium.
That’s to the southeast of Brussels.
The members were all over the city.
There was 50 metre between them.
-
If the victim becomes aware
of the harassment
then he will resist.
Generally,
this is the situation
of people who out themselves
as a
targeted individual.
Then the goal changes:
the victim has to be removed
as quickly as possible
from society
so he can’t spread what he knows:
-
prison,
-
bedlam,
-
forced suicide,
-
murder.
In this case,
they will first toy some time
with the victim
to make him fear for his life.
Then they suddenly kill him.
The surveillance of a targeted individual implies
that he’s surveilled
by several dozens of members of the police
and military secret service per day.
The interference in his private life
is more effective
when it’s insidious,
thus facilitating the general approval
of the thesis of mental illness.
A gang stalking campaign is successful
if the victim can’t prove the harassment.
The political success of these actions
lies in the number of investigations
carried out against offenders and criminals
who have been at a certain moment
in the immediate circle
of the victim of harassment
while avoiding
that the victim understands the fact
that he’s the pawn
that serves as a starting point
in the identification of suspect persons.
These persons will proactively be investigated
later.
The circle of a targeted individual
or an important individual
is always placed under surveillance.
Lookalikes of the circle of the victim are used
by the forces of law and order
to detect the persons
who are informed of the characteristics
of the circle of the victim.
So the victim is a disposable object
around which the network is built.
Who the victim is and what he has done
doesn’t matter at any point in the procedure.
The network is the political goal.
The
characteristic property
of political gang stalking is
that they make the victim appear crazy.
All these categories are gang stalkers:
-
nurses,
-
ambulances,
-
firemen,
-
private and public security companies,
-
banks,
-
managers of institutions,
-
embassies,
-
harbour master’s offices,
-
psychiatry,
-
some private institutions like universities.
Gang stalking has been observed
for 12 months
in a French speaking university in Belgium.
Gang stalkers collect information from the private life
of their victim.
Then this information is fed
through the media
to the victim.
Victims call this
media feedback.
The right name is
macro counter-espionage.
In Belgium the Communications Service
of the Ministry of Home Affairs
delivers the
ingredients
to the media.
This can be, for example,
a first name.
Then the media have to build
the news item around this word.
For example,
when a child is missing,
then the news item might be read by a journalist
with the name Vandeputte,
which is Dutch for Dutroux.
For example,
when a person with Down’s syndrome is in the news
then the news anchor won’t say his name,
except if he has the same family name as the victim.
The media are sponsored by political persons.
The media get their information from police and intelligence services.
So they have no choice.
They have to cooperate.
The goal is to stop criminal actions
of apolitical networks
by showing
that the government can do the same espionage
as the apolitical networks.
Some subjects are missing in his articles:
-
Freemasonry,
-
mind control,
-
electronic harassment,
-
voice to skull,
-
implants,
-
satanism.
(There are strong hints
that the gang stalkers are a
satanist
cult.
Currently we can’t prove that.
But, clearly, there’s more
that we don’t know yet.)
-
He treats it as a national problem.
For example,
he explains why Belgian victims hear details
from their private life
in the Belgian news on TV,
but he doesn’t explain why
they experience the same
with TV channels
of many other countries.
We know more categories of gang stalkers:
-
medical doctors,
-
dentists,
-
bus drivers,
-
train drivers,
-
taxi drivers,
-
personnel of utility companies (gas, electricity, telephone, cable TV and so on),
-
private and public gardening services,
-
teachers.
Gang stalking is performed
as much as possible
at the expense of their employers and the government.
So we see many stalkers
who have to travel for their job.
Some questions remain unanswered:
-
Why do targets experience the same harassments
in every country they go,
even in a country
that is an enemy
of their country of origin?
-
Why are nearly all victims single women and gay men?
-
Why are most victims female?
If this is about fighting crime,
then 90% of the victims should be male,
because 90% of all crime
is done by men.
-
Why do all the police in the world
deny that gang stalking exists?
-
Why are networks like
Al Qaeda
or
Hezbollah
never attacked with gang stalking?
-
Why did no one ever admit
that he was a gang stalker?
People have admitted
that they were a spy, informant,
Freemason, Mafia member, hitman or terrorist.
Outing oneself as a gang stalker
seems to be a problem of a higher order.
Most victims are not in a position
to teach you something about organized crime.
In the past,
the victims of the state
were usually deaf, blind, handicapped,
in the mental hospital or a home for the elderly.
So it looks more as if this is not about fighting crime,
but about getting rid of people who can be missed,
as they did in Nazi Germany.
So now we open our mind
for the mind control atrocities of the past
and see whether we find the answer there.
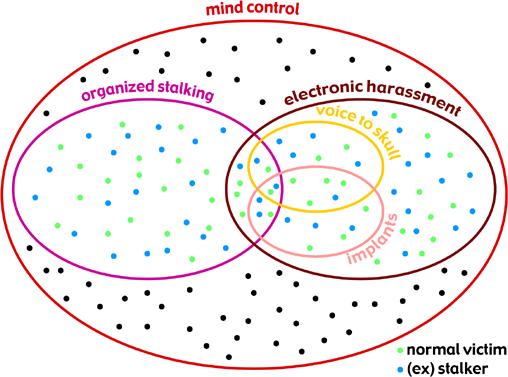
Mind control
is the systematic use
of unethically manipulative methods
to persuade others to conform
to the wishes of the manipulator.
Gang stalking
is a sort of mind control.
Gang stalking is a hate crime.
Electronic harassment
is another sort of mind control.
Electronic harassment is the use of electronic devices
to harass, torture, and/or physically harm a person,
or even the pets of the victim.
Many electronic devices can have a negative side effect on your health.
So they can be used for harassment.
About 50% of gang stalking victims experience
also electronic harassment.
Voice to skull
is a sort of electronic harassment.
Many gang stalking victims hear voices.
We suppose that the perpetrators use voice to skull
to harass and hypnotize their victims.
Implants
are a sort of electronic harassment.
It’s the most invasive type of stalking.
Some implant victims don’t experience gang stalking.
Gang stalking victims see them as
medical experimentees.
Mind control victims are very much like prisoners of war
who have been tortured.
The difference is
that they don’t know
why they have been tortured,
they don’t have their own army or support system,
they have been tortured by citizens of their own country,
and the torture is generally ongoing.
Rather than any sort of sympathy or respect
for having
served their country
by being selected for exploitation and torture
for the sake of what is called
national security
or
freedom,
these veterans of mind control abuse
are subjected to ridicule and abuse.
The psychological torture,
and often the physical torture,
is ongoing.
The origin of gang stalking is the
Vehmic tribunal
in Germany.
It’s called
Vehmgericht
in German.
It looked very much like Freemasonry.
It was introduced by
Charlemagne
to get the areas
that he conquered on the Germans
under control.
This goal is different from what Desurmont has described.
Later the
Stasi
developed the current methods of gang stalking.
They were copied by many other countries.
The goal of the Stasi was
to make people stop damaging communism.
So gang stalking isn’t new.
It exists already 800 years in its current form.
But, this is new:
- It’s a world wide network.
- They use instant electronic communication.
- They use electronic weapons.
Today, the 21st degree of the
Scottish Rite
of Freemasonry
is a representation of the Vehmic tribunal.
(Source:
Mackeys encyclopedia of Freemasonry.)
Read more on the Vehmic tribunal
in
Gangstalking — The Forbidden Book
chapter
1.f. Secret societies
(page 63 and following)
(PDF, 60.9 MB, 522 pages, readability 73%, reading age 10).
In 1956 Edgar Hoover ordered the start of COINTELPRO.
He was the head of the FBI.
In 1971 COINTELPRO stopped.
In 1972 Roger Tolces invented the word
electronic harassment.
He’s a private investigator.
In 1973 Dr. Joseph Sharp demonstrated voice to skull.
He worked for the Walter Reed Army Institute of Research.
In 1976 the congressional hearings about COINTELPRO concluded.
No one was ever punished.
No stalker has been exposed.
Around 1980 COINTELPRO on steroids started worldwide.
The name of the program is unknown.
In 1992 Julianne McKinney started the
anti-psychotronics movement.
She had worked 40 years as a Military Intelligence Officer.
In 1993 Norma Cross and Eleanor White
invented the word
gang stalking.
Eleanor White is a retired electronics engineer
who used to work for the U.S. Army.
In 1999 Eleanor White started the
www.raven1.net
website.
In 2001
David Lawson described gang stalking
in his book
Terrorist stalking in America.
He’s a private investigator from Florida.
In 2006 Jean-Nicolas Desurmont published an article about gang stalking.
He’s a criminologist.
In 2006 the US Army confirmed that
they use through-wall microwave body heating
to mimic fever to incapacitate people.
This takes between 15 and 30 minutes.
In 2007 David Lawson
published a second book about gang stalking.
In 2008 gang stalking was discussed
during a congress for criminologists in Barcelona.
In 2011 Larry Richard acknowledged gang stalking on TV.
He’s a police Lieutenant.
In 2011 Ted Gunderson
made an official statement about gang stalking.
He was a former FBI agent.
In 2011 Amy Anderson filed the first official complaint
that mentions electronic harassment.
In 2013 the Catholic Church of Switzerland
was the first large organization
to support our claims.
A few organizations and professionals acknowledge gang stalking, electronic harassment and/or implants.
They are not many, but, they cannot be ignored either.
The following organizations acknowledge gang stalking, electronic harassment and implants:
-
The Catholic Church of Switzerland
published a
long text in German about mind control
in which they confirm:
-
mind reading,
-
behavior modification,
-
change of thought, religion and sexual preference,
-
control of feelings,
-
chips control body, mind and dreams,
-
psychotronic generators,
-
brain transmitters,
-
voice to skull.
Download
the complete text
(PDF, 14.5 MB, 154 pages, readability 18%, reading age 19).
The following professionals acknowledge gang stalking, electronic harassment and/or implants:
Criminologists:
Engineers:
-
Eleanor White (electronics engineer)
-
Sergei Baranov (electrical engineer)
-
Tatyana Baranova (chemical engineer)
Former FBI agents:
-
Gerald Sosbee
-
† Ted Gunderson
Former Intelligence officers:
Former journalists:
Former judges:
-
Gerald Sosbee (Judge of City Court and Magistrate of the State of Texas)
Former Military Intelligence officers:
Former Navy:
-
† Aaron Alexis (Navy yard shooter)
-
Gary Simmons
Former NSA agents:
Former police instructors:
Former police officers:
-
Gerald Sosbee
-
Ken Baker
-
Lars Drudgaard
Former presidents:
Former private investigators:
Former university instructors:
-
Gerald Sosbee
-
Gloria Naylor
Lawyers:
-
Cheryl Welsh
-
Gerald Sosbee
-
Keith Labella
Medical doctors:
-
Dr. Anna Fubini (general practitioner)
-
Dr. John Hall (anesthesiologist)
-
Dr. Nick Begich (general practitioner)
-
Dr. Rauni Kilde (former chief medical officer of Finland)
-
Dr. Terry Robertson (anesthesiologist)
-
Dr. Vadim Baranov (general practitioner)
Politicians:
-
David Larson (director of the Bighorn-Desert View water agency)
Private investigators:
-
David Lawson
-
Roger Tolces
-
† Ted Gunderson
Sociologists:
Writers:
-
Alfred Webre
-
David Lawson
“Terrorist stalking in America”
-
Dr. Nick Begich
“Controlling the human mind - the technologies of political control or tools for peak performance”
-
Dr. Seth Farber (doctorate in psychology)
“The spiritual gift of madness: the failure of psychiatry and the rise of the Mad Pride movement”
-
Elizabeth Sullivan
“My life changed forever - the years I have lost as a target of organized stalking”
-
Gloria Naylor
“1996”
-
Jewel Krayan
“Electronic torture, electronic rape - technology and gang stalking at the post office”
-
Jørgen Christiansen
“The history of mind control from ancient times until now”
-
Maud Oortwijn
“Orange bruises”
-
Michael Bell
“The invisible crime”
-
Robert Näslund
“Hjärnprojekt - min egen historia”
Stalking
is unwanted pursuit, following or harassment.
Jean-Nicolas Desurmont
claims
that 1% of all men
and 2% of all women
are being stalked by multiple stalkers.
The
National Centre for Victims of Crime
of the USA
Department of Justice
has a website:
www.VictimsOfCrime.org
where they published statistics
about stalking victims of 18 years old or older.
Click on the image to see the original picture.
They don’t publish numbers
about victims of multiple stalkers.
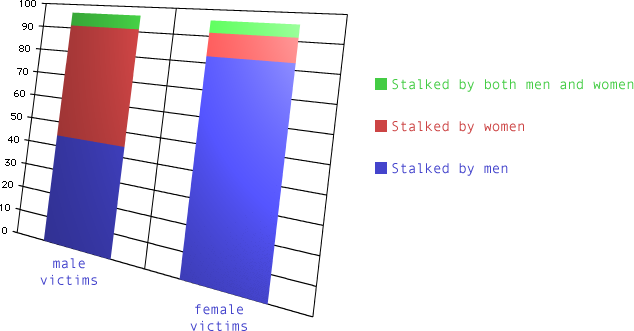
But, the statistics show
that about 5% of stalking victims
is a victim of at least one man
plus
one woman.
This allows the following interesting calculation.
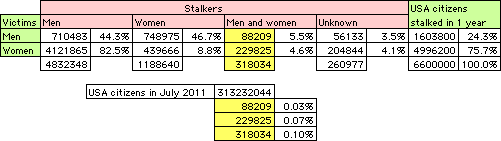
The statistics show
that about one in 1,000 persons
is an 18 years old or older
victim of stalking
by at least one man
plus
one woman:
multiple stalkers.
We may assume that
the number of people who are stalked by two men
and
the number of people who are stalked by two women
is equal to
the number of people who are stalked by one man
plus
one woman.
It shows
that about 3 in 1,000 persons
are 18 years old or older
victims of stalking
by at least 2 persons.
So if you live in a city with 10,000 citizens
then there should be 30 persons
of 18 years old or older
who experience this.
That’s about one person in every 4 streets.
It shows
that stalking by multiple stalkers isn’t rare.
The expressions
targeted individual,
mind control,
gang stalking,
electronic harassment
and
voice to skull
have something in common:
several ordinary words describe something controversial.
One of the results is that
when people want to describe gang stalking,
then they will write complex sentences
that are too difficult for children.
These expressions make it more difficult
to get the word out.
The victims call themselves
targeted individuals.
In June 2013,
there were about 1,400 persons
who have outed themselves as a victim.
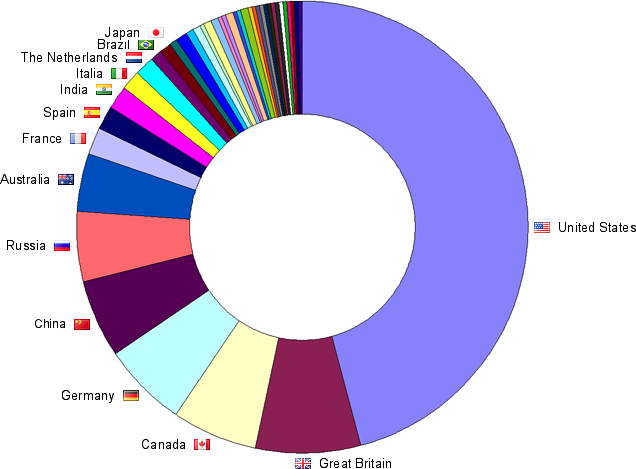
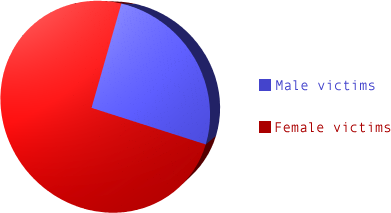
60% of all victims are women.
Most of them are independent women,
who live alone
and who want to make a career.
40% of all victims are men.
98% of them are gay.
Proud men with a high self-esteem
attract this harassment.
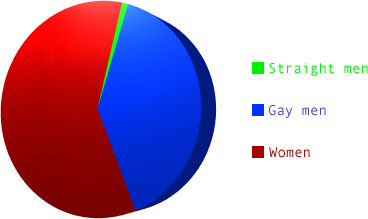
These charts show
that the distribution of
gang stalking victims
is totally different from
the distribution of
schizophrenia.
These charts prove that the victims are not mentally ill.
Most victims have in common:
-
They are perceived as not heterosexual enough.
(They are not married, or they don’t have children.)
-
Their family has connections with the army or security services.
Victims of gang stalking by the state
have to wonder their whole life
who is doing this to them and why.
I find this obvious questions.
If you are a victim,
then you certainly deserve to know the answer.
There are two theories:
-
In the USA they believe that
the secret services organize gang stalking
and that these secret services are populated by Freemasons.
-
In the UK they believe that
the Freemasons organize gang stalking
and that these Freemasons use the secret services
to push their agenda.
I follow the British theory.
As far as I know,
Freemasonry is the only organization
that is so corrupt and so mentally insane
that it could be responsible
for organizing gang stalking.
Clearly, there are relatively more victims
in countries where
there are relatively more
Freemasons.
This doesn’t mean that all gang stalkers are Freemasons.
The number of gang stalkers
is much higher
than the number of regular and accepted Freemasons.
(The whisperers say 96% of the population.)
The gang stalkers are a secret society,
and they are satanists,
but they are no regular and accepted Freemasons.
Many gang stalkers are too young,
too poor,
or too abnormal to apply for membership.
Gang stalkers who are not a Freemason are called
familiars.
They are people who help Freemasons
because they hope
that some day
they will get an invitation
to become Freemason.
I know that it sounds far-fetched:
-
Freemasons organize gang stalking.
-
Freemasons are satanists.
I’m aware that Freemasons won’t like it
when I write like that.
I also read complaints on other websites.
Now look at the evidence:
If you want to learn to know the Freemasons,
then listen to the people who left Freemasonry.
Jim Shaw was a Freemason from Florida,
who left Freemasonry,
and who converted to Christianity.
He claimed to be a 33rd degree Freemason,
but I ignore whether that was true.
He wrote the book
Deadly Deception.
This is a quote from Jim Shaw
that is circulating on the internet:
“All have mental questions
to even join in the first place.
To be so corrupt…
so criminally insane,
mentally insane…
to gangstalk the helpless…
to murder the helpless…
to teach their children
to hate the "profane,"
you and I,
the non masons…
to worship not 1 but 3 evil gods…
to join something and swear to,
not having NO idea what you have sworn to…
pure insanity !!!…
to enjoy little boys and girls…
even their own children…
and their mothers…
themselves in the rituals.”
This quote says clearly:
“to gangstalk the helpless…”
In July 1889,
Albert Pike was the Sovereign Pontiff
of the Universal Freemasonry.
He wrote in a letter:
“The true and pure philosophic religion is the belief in Lucifer, the equal of God.”
Clearly, Freemasons organize gang stalking
because they are doing their master,
the Satan,
a favor.
But, there’s more.
Now take a look at this.
These are the things
that Freemasons hate most of all:
-
celibacy,
-
homosexuality.
It’s very easy to connect the dots:
gang stalking is organized by Freemasons
because they believe that you HAVE to reproduce.
Now take a look at their symbol, the square and compass:

-
The square represents the vagina or the earth.
-
The compass represents the phallus or the sun
which impregnates the earth
with life-producing rays.
-
The G means Generation: creation of new life.
So the symbol means
phallus in uterus God.
It means that hetero sex is God.
Of course,
a secret organization
that pledges oaths of persecution
and that is obsessed with reproduction
has to be really bad news for single women and gay men,
the usual victims of gang stalking.
This becomes visual in gang stalking.
This is how they revealed themselves.
The word
Freemasonry
is now silently being replaced with the word
gang stalking
because that’s the activity for which we know them best.
Read more about Freemasonry on
https://archive.org/details/FreemasonryExposedByFreemasons
If you recognize several events
on the following list,
then you are probably a victim of gang stalking.
-
All your family, friendship,
and business relationships are going sour
and you have done nothing to cause this.
-
You see many times more than usual:
-
people with red jackets,
-
red cars,
-
white cars,
-
SUV’s
(sport utility vehicle,
something between car and Jeep),
-
scooters.
-
You experience often loud noise:
-
trains go over bridges exactly
when you go over the bridge,
-
sirens,
-
neighbors are drilling in the wall,
-
neighbors are hammering on the wall,
-
neighbors buy annoying dogs that keep barking,
-
neighbors send annoying dogs to their garden
when you go to your garden,
-
scooters,
-
crying babies.
-
You hear
directed conversations.
These are conversations that are directed
at you but in a deniable way.
For example:
-
Someone walks his dog.
When he passes you he says
“Stupid fool”
to his dog.
-
You eat much because it’s cold.
When you leave there’s a man
who says
“You eat too much”
to his little child.
-
There are many variants with cell phones.
-
You are often being gassed:
-
you’re being sprayed with pesticide in the library,
-
fumes from scooters, trucks, tractors, busses, boats,
-
the neighbors have a leaking oil reservoir,
-
the chimneys of the neighbors are too low.
-
You experience many times more than usual:
-
wrong number calls,
-
street lights go out or go on
when you walk or drive under them,
-
break-ins without leaving trace,
-
small thefts,
-
things disappear
and reappear somewhere else,
-
things are moved or rearranged,
-
sabotage at home and at work,
-
your path is blocked
when you walk or drive.
For example:
-
people walk straight into you,
-
people cross the street
or cycling path without looking at you,
-
someone slips ahead of you
at the bank machine or
grocery checkout,
-
cars are in unexpected
places in parking lots,
-
cars are at the worst moment
at the worst place
-
when you arrive at an intersection,
-
when you want to make a left turn,
-
when the road has become
narrower because of an obstacle on the road
(and these obstacles occur more than normal),
-
there are more people
who arrive before you
at shops
than there are people who leave,
-
people form a queue
ahead of you
in shops,
-
favorite products are sold out,
-
things are thrown in your garden,
-
garbage is not picked up.
-
problems with electronics:
-
your bankcard is
“unreadable”
in shops,
-
car electronics,
-
computer errors,
-
hacking,
-
e-mail problems,
-
cell phone problems,
-
telephones with static or tones or
echoes.
-
Names are being changed:
-
the street where you used to live,
-
the school where you went,
-
the diploma that you have,
-
the company that you have worked for.
-
You experience rude behavior from people
that you don’t know, for no reason.
-
You see hints
that they know something about you:
-
in the media: TV, radio,
newspapers, magazines,
songs, publicity,
-
in new products,
-
in advertisements.
For example, you see ads
for the things that you have,
with ridiculous prices,
-
in the names
of new personalities
or people who contact you by letter,
-
in passwords,
-
in nicknames,
-
in URLs,
-
in numbers of letters.
-
Products that you used to buy
because you were satisfied
about them
are suddenly changed
or replaced
so that you are not satisfied
anymore:
-
food,
-
radio stations,
-
TV programs,
-
channels on cable TV.
If you recognize several events
on the following list,
then you are probably a victim of electronic harassment.
-
Fake sounds:
-
ear ringing:
a loud steady tone,
like a dialling tone.
This is generally in the left ear.
(Left means no, right means yes.)
-
voices in your head,
-
telephone ringing,
-
clock ringing,
-
knocking on your door,
-
loud bird calls that follow you everywhere.
-
You can’t get a song out of your head.
-
Unusual headache.
For example,
every Friday at 11 AM
you get suddenly a debilitating headache
that is suddenly over on Saturday at 11 AM.
This continues for dozens of years.
-
Fake vision:
-
You see vivid 3D images while being awake,
with eyes open or closed.
-
You see
“falling stars.”
-
You recognize someone that you have never met.
-
You see
“edges”
around everything.
-
People seem to appear from nowhere
and are suddenly on the road.
(The person was temporarily removed from your vision.
What your eyes see is mixed with an image of the empty road,
and the result is sent to your brain.)
-
Sleep disturbance:
-
Controlled awakening:
-
every day at precisely the same time,
-
every hour at precisely the hour,
1 AM, 2 AM, 3 AM and so on,
-
false awakening.
(You dream that you wake up,
sometimes several times after each other.)
-
Controlled sleep:
-
You can’t go back to sleep.
-
You sleep much too long.
-
Controlled dreams:
-
You see red and blue blurs
before you fall asleep.
-
A voice talks to you in your dream.
-
People like your family
laugh at you in your dream.
-
You dream always about people that you never saw before.
They never return in a dream.
-
You have dreams like HD cinema,
with crisp and clear rectangular images
with bright colors,
many people and much activity.
The dreams are inside buildings without windows.
If there are windows
then you can’t look through them.
-
You have series of dreams where
every dream continues
where the previous dream ended.
-
You never dream about sex.
Instead, you have
“neutral”
dreams.
-
You never dream about your hobbies.
-
You dream that you have strange headaches.
For example,
you dream that your head is electrocuted.
-
“bee stings”
(like hot needles deep in your flesh),
-
limbs jerking wildly,
-
extremely powerful itching
which may start as small electrical shocks.
-
Controlled body functions:
-
very fast heartbeat while being relaxed
(not having exercised recently),
-
very high body heat,
no fever, relaxed,
cool surroundings,
-
vibration of a large area of your body,
or nearby objects which should not vibrate normally,
-
sudden
“drop-you-in-your-tracks”
fatigue at
times you should not be tired.
-
You wake up with a very fast heartbeat
and high blood pressure.
-
Controlled behavior:
-
You buy things that you regret.
-
You didn’t buy things that you wanted.
-
You have urges to go somewhere
that you don’t need to go
or at times that you wouldn’t go there.
-
You go to a shop or library
although you should remember
that it’s closed at this day of week.
-
Controlled imagination:
-
You write or say things
that you wouldn’t normally
want to write or say,
-
You sing along with a
“song in your head.”
But, sometimes the tone goes down.
So you have to sing lower and lower.
-
You want to be funny,
but they see it different.
-
Your erotic fantasy
is systematically replaced
with things that are not erotic,
and that you don’t want.
For example, if you think of your lover
then he/she is replaced with a photograph
of the house of your parents
that you didn’t see in 20 years,
so it becomes impossible to think of your lover.
-
Observation in your house:
-
People repeat something in public
that was said privately in your home.
-
Neighbors make sounds
that are synchronized
with what you’re doing.
-
Neighbors leave
at the same moment
that you leave.
-
When you leave
and you come back
then you see that they have tampered
with what you were doing.
This is probably done with pinhole cameras
and microphones.
I don’t believe
that they would use through-wall radar
when a pinhole camera is much cheaper
and gives a much better image.
-
Memory problems:
-
Blocked memories.
You forget things.
For example, you turn a page
in a magazine,
you see a photograph
of your idol
but you can’t remember his name.
-
Inserted memories.
For example, you remember
that you read something
in a letter.
But, there was no such letter.
(It was a dream.)
-
Erased memories.
You have a good idea,
but suddenly you loose the idea
and how hard you try,
it doesn’t come back.
-
Side effects:
-
Batteries are drained rapidly.
-
Repeated instances where it seems
that your mind is being read.
For example, someone repeats
what you were thinking.
This can be done with subvocal recognition
or remote neural monitoring.
-
Repeated instances where it seems
that your mind is being changed.
For example,
you were thinking of a lion
while sitting on the train.
When you leave the railway station,
there’s a billboard with a lion.
John Finch from Australia collects the victim stories.
If you want to out yourself as a victim,
then you can send your story to:
John Finch,
5/8 Kemp Street,
Thornbury, Vic 3071,
Australia,
TEL: 0424009627
tijohnfinch@gmail.com
This is one of the most useful things
that you can do as a victim.
Perps assume that no one will ever hear
what happened to you,
because gang stalking sites and victim blogs
are only visited by a handful of victims,
so the perps can do whatever they want.
This changes when John Finch
sends your story to a long list
of email addresses.
Start your message like this:
NAME: John Smith
Citizenship: USA
Year Torture/Abuse Began: 2001
Email: john.smith@yahoo.com
WEB: johnsmith.blogspot.com
Later you can update your story.
Your new message will be appended to your old story.
So you write only what’s new.
These testimonies show that
gang stalking victims
are experiencing the same specific harassments
all over the world
while
the experiences of
schizophrenics
are more general and more different.
These testimonies prove that the victims are not mentally ill.
Sooner or later,
a targeted individual will complain of
hearing voices.
Voice to skull harassment
is the most familiar type of electronic harassment.
Voice to skull was first demonstrated in 1973
by Dr. Joseph Sharp.

In the article Microwaves and Behavior
on page 396
in the
American Psychologist
of March 1975
Dr. Don R. Justesen says clearly:
Sharp and Grove (Note 2) found that appropriate modulation of microwave energy can result in direct “wireless” and “receiverless” communication of SPEECH.
The definition of voice to skull
appeared a few years ago
on a website of the US army.
You can still
view it on www.archive.org.
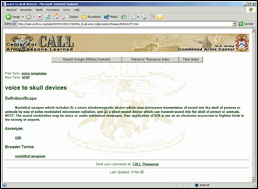
Note that they call it a
weapon.
So it’s not a communication device
like a telephone.
There’s a countermeasure that works:
an underground facility
with vacuum panels against the walls, the ceilings and the floors.
Many armies in the world have such facilities.
Download
the technical details of voice to skull
(PDF, 404 K, 17 pages, readability 65%, reading age 12).
8 men have proven that they have implants.
I made a separate website
which is dedicated to these cases:
www.implant-victims.com.

One person has caused a massacre
because he believed
that he was attacked with gang stalking
and electronic harassment.
I made a separate website
which is dedicated to such cases:
www.GangstalkerDown.com.

In October 2008 I started to collect
everything about gang stalking that I could find.
The most popular item on this website is
the book with victim stories from the USA.
Forwood’s book is also very popular.
The most interrupted download is my own book,
mainly because it’s such a big file.
So before you start to download,
be sure that you want to download such a big file.
The books are sorted in order of readability.
Books:
-
Control Factor — The movie explained
(1)
by Cliff Huylebroeck
(PDF, 6.6 MB, 187 pages, readability 77%, reading age 9).
This book looks a bit like a comic strip album.
It tells the story of the movie
and gives you some background information.
A few years ago,
they started to distribute
a comic strip album
that makes people believe
that they have schizophrenia
if they believe this sort of things.
So there should also be a comic strip album
that tells people that they are normal
if they believe this sort of things.
This science fiction movie
contains much material
of which we suppose that it exists,
of which we can prove that it exists,
and of which we know that reality is even worse.
-
Gangstalking — The Forbidden Book
(2)
by Cliff Huylebroeck
(PDF, 60.9 MB, 522 pages, readability 73%, reading age 10).
This book is for victims and open-minded people.
It’s written in short sentences with simple grammar.
It’s readable for people who are not fluent in English.
And it has many pictures, cartoons and appendices.
The main idea of this book is
that all those gang stalkers
are a secret society.
This isn’t mentioned in the other books.
21%-23% of all 11-13 year old Irish children hear voices.
So there had to be a book that is readable for 10 year old children.
You may also want to
download
the
New York
font for Windows
(zipped TrueType font, 36 K)
otherwise, it will be substituted with a similar font.
-
Bridging the gap
(3)
by GmB Bailey
(PDF, 3.3 MB, 116 pages, readability 52%, reading age 15).
The goal is to maintain state control at all costs.
-
The hidden evil
(4)
by Mark Rich
(PDF, 708 K, 82 pages, readability 51%, reading age 15).
Mark Rich is an activist from Massachusetts in the USA.
His first experience was mobbing.
This gets much attention in his book.
This book is for victims and open-minded people.
He has done much research.
His book contains quotes
that you will probably not find elsewhere.
I have also a
beautified book
(5)
(PDF, 360 K, 148 pages, readability 51%, reading age 15).
-
 Du harcèlement en réseau au harcèlement global
(6)
by Josselyne Abadie
(PDF, 720 K, 24 pages, readability 50%, reading age 15).
This booklet taught me nothing new,
but for people who speak only French,
this will be a good introduction.
Du harcèlement en réseau au harcèlement global
(6)
by Josselyne Abadie
(PDF, 720 K, 24 pages, readability 50%, reading age 15).
This booklet taught me nothing new,
but for people who speak only French,
this will be a good introduction.
-
Gang-stalking and mind-control — The destruction of society through community spying networks
(7)
by A. K. Forwood
(PDF, 400 K, 100 pages, readability 40%, reading age 19).
The fascist government seeks to control every individual completely.
He blames government as well as corporations.
-
Psychiatry committing fraud
(8)
by the Citizens Commission on Human Rights
(CCHR)
(PDF, 1.8 MB, 52 pages, readability 37%, reading age 18).
This publication was sponsored by Scientology.
-
Gang stalking is becoming a problem
(9)
by Cliff Huylebroeck
(PDF, 724 K, 150 pages, readability 30%, reading age 21).
This is the English translation of Desurmont’s text.
-
The microchipping of America: human rights implications of human bar codes
(10)
by Gena Mason
(PDF, 208 K, 46 pages, readability 28%, reading age 19).
-
 Mind control
(11)
by the Catholic Church of Switzerland,
beautified by Cliff Huylebroeck
(PDF, 14.5 MB, 154 pages, readability 18%, reading age 19).
This is the first large organization that confirms our claims.
Mind control
(11)
by the Catholic Church of Switzerland,
beautified by Cliff Huylebroeck
(PDF, 14.5 MB, 154 pages, readability 18%, reading age 19).
This is the first large organization that confirms our claims.
Early stuff
—
Eleanor White and Norma Cross
were the first activists
in the field of gang stalking.
They didn’t treat mobbing
as a type of gang stalking.
Their definition of gang stalking
describes only
gang stalking by the state.
This provokes immediately the embarrassing question:
“Who would want to do this and why?”
and the embarrassing answer:
“I never heard about this.”
-
More gang stalking
(12)
by Eleanor White
(PDF, 7 MB, 395 pages, readability 64%, reading age 11).
She explains all sorts of technologies that can be used for harassment.
She teaches how to do activism.
-
CATCH brochure
(13)
by Norma Cross
(PDF, 264 K, 25 pages, readability 51%, reading age 14).
CATCH was the first website about gang stalking.
-






 Organized stalking: information for people for whom this crime is a new issue
(14)
by Eleanor White
(PDF, 3.4 MB, 449 pages, readability 51%, reading age 15).
This book is for people who never heard of gang stalking.
If you are a victim,
and you want to show something
to sceptical people,
then this book is the best choice.
She gives you clear facts, no rant.
It was translated by volunteers.
Organized stalking: information for people for whom this crime is a new issue
(14)
by Eleanor White
(PDF, 3.4 MB, 449 pages, readability 51%, reading age 15).
This book is for people who never heard of gang stalking.
If you are a victim,
and you want to show something
to sceptical people,
then this book is the best choice.
She gives you clear facts, no rant.
It was translated by volunteers.
-
Raven1 book
(15)
by Cliff Huylebroeck
(PDF, 53.4 MB, 5081 pages).
This is the PDF version of Eleanor White’s
www.raven1.net.
This used to be the most well-known website about gang stalking.
It was online from 1999 to 2013.
Electronic diagrams:
-
Electronics behind voice to skull
(16)
by Cliff Huylebroeck
(PDF, 404 K, 17 pages, readability 65%, reading age 12).
-
Microwave voice to skull simulated with a 555 chip tachometer circuit
(17)
by Cliff Huylebroeck
(PDF, 12 K, 1 page).
Eleanor White designed this circuit
to simulate Dr. Sharp’s microwave voice to skull method.
She has built such a device.
-
Silent sound demo device
(18)
by Cliff Huylebroeck
(PDF, 20 K, 1 page).
Eleanor White designed this device
as an exact replica of Lowery’s patent 5,159,703.
She has built such a device.
Reports:
-
EXHIBIT B — Dr. Emily A. Keram Report
(19)
by Dr. Emily A. Keram
(PDF, 120 K, 20 pages, readability 54%, reading age 14).
She had worked 20 years as a psychiatrist
at the US Department of Veterans Affairs.
She examined the Saudi national Shaker Aamer,
who resided in the UK,
and who was sent to a detention centre in Guantanamo
as an Al Qaeda suspect.
He describes his torture with electronic harassment.
His description is typical of the experiences of targeted individuals.

-
Microwave harassment and mind-control experimentation
(20)
by Julianne McKinney
(PDF, 136 K, 84 pages, readability 33%, reading age 19).
She had worked 40 years as a Military Intelligence Officer.
She says that the devices are concealed
as upright pianos, microwave ovens,
and oversized stereo speakers,
measuring approximately 5’ in height x 3’ x 3’.
-
US electromagnetic weapons and human rights
(21)
by Peter Phillips, Professor of Sociology,
Lew Brown, Psychologist,
and Bridget Thornton, senior level History major,
Sonoma State University
(PDF, 312 K, 48 pages, readability 32%, reading age 20).
This article
was published in December 2006.
This is a difficult text.
It starts with a long history.
The interesting part is in the middle.
Here are some quotes:
Page 11:
In the late 1950s,
a right-wing cadre of men within the new CIA
was busy building secret armies,
planning assassinations,
and generally devising plans for world domination
that still play out today.
Page 14:
Here,
they describe Nikola Tesla’s plans for fantastic weapons.
Page 15:
In 1934 Tesla offers to build a
Death Ray
that would make the power of an opponent’s air force obsolete.
Page 25:
The Russians banned all EMF weapons in 2001.
Page 26:
Americans have little idea
about the research concerning the capabilities of electromagnetism,
directed acoustics,
or computer-human interfacing.
The majority of Americans do not know
that we are currently using these new-concept weapons
in Iraq and Afghanistan.
Page 29:
Of great concern is the research being conducted at DARPA,
which is trying to revolutionize
the way soldiers receive information,
respond to orders,
adapt to stress,
and perform while sleep deprived.
Page 30:
In essence,
Augmented Cognition allows a human to interact
with a computer through brain waves.
The idea is to enhance a person’s cognitive capabilities
in the area of memory,
learning,
attention,
visualization,
and decision-making.
[…]
The increase in human-computer relations
and the ability to manipulate and control
a person’s senses,
memory,
and neural output has wide implications.
[…]
The basic ability to enter a person’s mind is not a futuristic fantasy. This is real and in prototype.
Page 33:
Dominant Remote Control seeks to control,
at a distance,
an enemy’s vehicles,
sensors,
communications,
and information systems and manipulate them for military purposes.
Page 38:
However,
hundreds of people continue to assert that a person or persons,
whom they do not know,
have been targeting them with electromagnetic weapons
in a widespread campaign
of either illegal experimentation or outright persecution.
[…]
These experiences involved a number of discrete phenomena:
1)
Hearing voices when no one was present.
2)
Feeling sensations of burning,
itching,
tickling,
or pressure with no apparent physical cause.
3)
Sleeplessness and anxiety as a result of
humming
or
buzzing.
4)
Loss of bodily control,
such as twitching or jerking of an arm or leg suddenly and without control.
5)
Unexpected emotional states,
such as a sudden overwhelming feeling of dread,
rage,
lust or sorrow that passes as quickly as it arises.
Articles:
-
Are ‘they’ watching?
(22)
by Lance Anderson
(PDF, 840 K, 4 pages, scanned article).
This is the first magazine article about gang stalking.
-
Gang stalking
(23)
by John B. Lopes
(PDF, 112 K, 2 pages, readability 57%, reading age 15).
A private detective explains gang stalking.
-
 La géocriminologie en contexte de gang-stalking
(24)
by criminologist Jean-Nicolas Desurmont
(PDF, 268 K, 28 pages, readability 43%, reading age 17).
This article centers on gang stalking by the Mafia.
La géocriminologie en contexte de gang-stalking
(24)
by criminologist Jean-Nicolas Desurmont
(PDF, 268 K, 28 pages, readability 43%, reading age 17).
This article centers on gang stalking by the Mafia.
-
 Vers une problématique du harcèlement criminel en réseau
(25)
by criminologist Jean-Nicolas Desurmont
(PDF, 172 K, 39 pages, readability 39%, reading age 19).
This article centers on gang stalking by the government.
Vers une problématique du harcèlement criminel en réseau
(25)
by criminologist Jean-Nicolas Desurmont
(PDF, 172 K, 39 pages, readability 39%, reading age 19).
This article centers on gang stalking by the government.
-
Microwaves and Behavior
(26)
by Dr. Don R. Justesen
(PDF, 92 K, 11 pages, readability 26%, reading age 20).
Dr. Justesen describes Dr. Sharp’s experiment with communication of speech through microwaves.
Statements:
-
Amy Anderson’s complaint
(27)
by Amy Anderson
(PDF, 5.2 MB, 6 pages, scanned article).
This is the first official complaint that mentions electronic harassment.
-
Ted Gunderson’s affidavit
(28)
by Ted Gunderson
(PDF, 656 K, 14 pages, readability 26%, reading age 20).
Former FBI agent Ted Gunderson makes an official statement about gang stalking.
Letters:
-
Bioeffects of selected nonlethal weapons
(29)
by Donald Friedman
(PDF, 4.1 MB, 20 pages, scanned article).
This is the first answer to a FOIA request that confirms that they incapacitate people by heating them with microwaves through the wall.
Emails:
Manifestos:
-
Manifesto against gang stalking
(32)
by Zaouali Youcef
(PDF, 156 K, 14 pages, readability 64%, reading age 12).
-
Manifesto against psychiatry
(33)
by Gene Zimmer
(PDF, 80 K, 57 pages, readability 49%, reading age 16).
-
Manifesto against Wikipedia
(34)
by Paulo Correa, M.Sc., Ph.D.,
Alexandra Correa, H.BA.,
Malgosia Askanas, Ph.D.
(PDF, 100 K, 17 pages, readability 38%, reading age 18).
-
Manifesto against FFCHS
(35)
(Freedom from Covert Harassment and Surveillance) by
www.FightGangStalking.com
(PDF, 344 K, 8 pages, readability 28%, reading age 23).
Victim stories:
-
The Americas
(36)
by John Finch and 600 victims
(PDF, 4.7 MB, 924 pages, readability 55%, reading age 15).
-
Europe
(37)
by John Finch and 300 victims
(PDF, 3.5 MB, 521 pages, readability 55%, reading age 15).
-
China and Asia-Pacific
(38)
by John Finch and 250 victims
(PDF, 2.7 MB, 267 pages, readability 53%, reading age 15).
-
South Asia, Middle East and Africa
(39)
by John Finch and 40 victims
(PDF, 648 K, 101 pages, readability 55%, reading age 15).
-
Russia and Belarus
(40)
by John Finch and 60 victims
(PDF, 360 K, 48 pages, readability 42%, reading age 16).
Kooky stuff:
-
Carl Clark interview
(41)
by Raum und Zeit magazine
(PDF, 2.3 MB, 10 pages, readability 67%, reading age 10).
Carl Clark claims to be an ex-perp
who was involved in gang stalking
but not in electronic harassment.
-
If you become a target of gang stalking…
(42)
by Miyoko Goto
(PDF, 88 K, 5 pages, readability 60%, reading age 13).
-
The silent massacre
(43)
by Max Williams
(PDF, 408 K, 73 pages, readability 51%, reading age 15).
Max Williams has a degree in history.
-
ICAACT phase III testing
(44)
by Jesse Beltran and Lars Drudgaard
(PDF, 8.7 MB, 53 pages, readability 33%, reading age 18).
They search electronic implants.
They tested a few people in a Faraday cage.
There are 44 eBooks on this page
with a total of 10449 pages.
Books written by scientists:
-
The technologies of political control or tools for peak performance
by Dr. Nick Begich,
2006.
Dr. Begich convinced the European Parliament
to vote resolution A4-0005/99
Resolution on the environment, security and foreign policy
which calls for an international convention
introducing a global ban
on all developments and deployments
of weapons which might enable
any form of manipulation of human beings.
They voted it on January 28, 1999.
Books written by investigators:
-
Terrorist stalking in America
by private investigator David Lawson,
2001.
-
Cause stalking
by private investigator David Lawson,
2007.
Books written by victims:
-
1996
by Gloria Naylor.
She’s a writer for theater, film and television.
She became a victim in 1996.
She described that year
using a fictional character.
-
My life changed forever - the years I have lost as a target of organized stalking
by Elizabeth Sullivan,
2008.
-
Orange bruises
by Maud Oortwijn from the Netherlands,
2014.
The Investigative Journal:
-
Greg Szymanski interviewed Julianne McKinney
on April 19, 2006
(zipped MP3, 9.9 MB, 45 minutes).
She had worked 40 years as a Military Intelligence Officer.
She says that they need to see you
whenever they want to target you
with electromagnetic weapons.
So they will come in your house
and install miniature cameras.
The electromagnetic weapons are installed
in the houses of your neighbors.
Your neighbors use the electromagnetic weapons.
Movies for victims and open-minded people:
-
Control Factor
with Adam Baldwin and Elizabeth Berkley
(2003, 84 minutes).
An average everyman discovers
that he’s the unwitting target
of an ultra secret domestic black operation
which centers on mind control.
Lance Bishop is almost shot at his office
by a self-proclaimed mercy killer,
who gets shot in time.
Then his life changes.
He hears a voice
that commands him to shoot his wife.
A detective is killed before his eyes
with an exotic weapon.
Then he has his first nervous breakdown.
At home he finds a CD that was sent by the shooter.
The shooter was some army psych
who did mind control research.
He gives him an address.
In the middle of the night
he goes to the address.
He meets Reggie,
who shows him a second video message.
Then the building is stormed
by a team that collects emotions.
Before he leaves, he gets a protective cap,
but he forgets to put it on.
The people on the street
are under the influence of the technology.
He has a second nervous breakdown,
but he can put the cap on.
He buys an electronic device to prove the harassment.
At home he discovers a man with a device
in the window at the other side of the street.
He tries to call help,
but his call is intercepted.
He discovers that his noisy neighbors
have been replaced with a tape recorder.
His wife removes his cap to clean his face.
He’s defenseless against the technology.
He has a third nervous breakdown.
Then he shoots his wife.
But, it was a dummy bullet.
She starts to behave like an agent and leaves.
He goes after her.
He discovers a local control center in the same building.
His wife knocks him out.
They wipe his memory.
His life continues as if nothing happened.
He has to take medication.
They irradiate him to impair his memory.
But, a dish that is glued together
remembers him of the events.
When they notice that his memory is back,
they decide to kill him.
But, Reggie arrives in time.
As the agents try to give Lance a heart attack,
Reggie grabs the gun and shoots an agent.
Lance and Reggie jump through the windows.
They fall in a garbage truck.
Phase 2 starts while they are in a pub:
mass behavioral modification.
They will cause civil disturbance.
Lance and Reggie buy weapons, but, they are robbed.
The gang is wearing the protective caps
that they have stolen.
Suddenly, they are free from the mind control.
They join Lance and Reggie.
Lance is discovered because he calls his wife.
The agents go after him, but his friends shoot them.
Lance and Reggie torture the team leader.
He reveals where the control center is: in the hospital.
He’s forced to call for backup.
Lance kills him with the heart attack weapon.
He removes his cap.
Now the agents can easily arrest him
and bring him to the hospital.
His wife has been ordered to execute him.
But, she wants to bring him alive to the Director,
so he can shoot him.
Then their son won’t have to grow up in hell.
Lance fails to kill the Director,
because he appeared as a hologram.
Watch it on YouTube
or
watch it on retro films India.
-
Dark Water
with Jennifer Connelly
(2005, theatre version of 107 minutes and DVD version of 103 minutes).

This movie was rated the best horror movie of 2005.
It’s about gang stalking because of a hostile divorce.
Kyle moves to New Jersey because his girlfriend lives there.
But, Dahlia moves with their daughter Cecilia to New York.
So it becomes more difficult for Kyle to see his daughter,
so he sues her.
He actually pays stalkers to make her appear insane
(you see this in scene 1:05:08, see the picture)
so she will appear unfit to raise the child and lose the trial.
But, it’s a spooky building.
They don’t say it directly,
but probably an abandoned girl was murdered
by the landlord and his helper,
and they dumped her in the water reservoir on top of the building.
Then strange things happen by leaking water.
So it’s never clear whether the perps are behind it,
or could it be the spirit of the dead girl.
Also, they start to hear voices, see the dead girl,
there’s remote body control.
You see also that Kyle follows the child to school,
and then it happens there too.
So the spooky things are caused by Kyle.
Also, when Dahlia has migraines,
you hear the sound of ultrasound scans.
These are references to electronic harassment.
But you’re never sure what is behind it.
It’s a horror movie!
Video games for victims and open-minded people:
-
Watch Dogs
(not yet released)

In this video game you control a vigilante.
All electronic devices in Chicago are linked
to the Central Operating System.
You can hack this system.
You can retrieve bank data and steal funds.
You can trigger malfunctions in equipment
to distract other characters.
You can change traffic lights to cause collisions.
You can use it to evade police and to track targets.
The goal of the game is
to kill a target or
make him flee to a large distance.
In this chapter
I will discuss all advertisements
that are related to gang stalking.
On September 26, 2012 the bogus group FFCHS placed this billboard in Rhoades.

The ad doesn’t contain the words
gang stalking
or
electronic harassment.
There are 18 words in the ad,
of which 17 start with a capital letter.
13 words are on a black background.
7 words are Italic.
5 words are in a narrow font.
So the readability is very low.
So the message is reduced to: call this number.
But, if you call this number,
then what?
Interception of calls is very common.
I designed these better billboards.
They address the reader directly.
This is clear, readable and colorful:

This is clearer, but less colorful and less attractive because it has no picture:

This is in grayscale:

This is Justin Bieber actually:

When people walk close to the billboard,
then you can try something artistic:

On July 16, 2013 the bogus group FFCHS placed this ad in the
Washington Post Express.

The ad is a letter which is addressed to the president.
This is very readable, in large white capital letters
on a black background.
So it’s not addressed to most readers.
The ad is screaming: don’t read me,
this is for the president.
The letter is Italic.
So the readability is very low.
The ad doesn’t contain the words
gang stalking
or
electronic harassment.
At the end of the letter
the reader learns that he can become the next victim.
It’s a waste of advertisement space.
The letter should have been on a web page.
Its link should have been in the ad.
Then there’s room for a real ad.
I designed this better ad.
It’s clear, readable and colorful.
It addresses the reader directly.

In January 2012 I started
www.hearingvoices-is-voicetoskull.com.
It was meant for people who realize
that they hear voices,
so they go to
Google
and search
hearing voices.
Then I explained what voice to skull is,
and I gave an introduction to gang stalking.
I thought that this website would attract
many people who hear voices.
But, the information on my website was mainly about gang stalking.
So it attracted mainly people who knew already what gang stalking is.
So I changed the plan.
I started this website.
The design is completely different:
it’s only one page.
The first website had many pages,
one for every subject.
But, people are used to slow links,
so they don’t follow links anymore.
Perps wrote a paragraph about gang stalking
in the Wikipedia article about stalking.
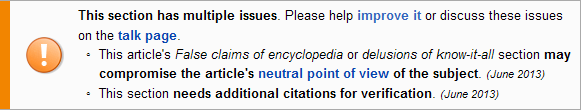
This paragraph is very negative for the victims.
It’s heavily guarded.
If you delete it
then they will revert it
almost immediately.
I’m sure[weasel words]
that they do this to influence the search engine results.
Most people will go to their search engine
and type
gang stalking wiki.
On June 4, 2013 I saw that
Google
returned 151,000 results
for
gang stalking wiki.
This was the top of the list:
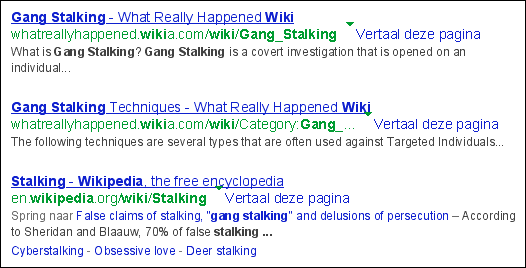
I wondered whether I could eventually
have a better ranking than Wikipedia
on top of this list.
Wikipedia is a large site,
but the word
gang
was only 4 times on the
Stalking
page.
I saw that
Google
returned some of my websites
as result # 1 when I searched for the words in their name.
So I knew that it was doable,
especially if I post large texts about
gang stalking.
On August 14 I googled
gang stalking wiki
and my site was already hit number 2.
If I add new text to this site,
then it can temporarily be number 1.
On December 16 I googled
gang stalking wiki:
Wikipedia is not scientific.
It’s not coherent.
For example,
on one page
they wrote
that Jesus is a historical person.
On another page
they wrote
that Jesus has never existed.
Wikipedia is not neutral.
It’s based on what people say on TV,
or write in a magazine.
That’s not a good reference.
Wikipedia won’t publish a dissenting opinion.
For example,
they won’t allow that you write about drone attacks
on a list of terrorist incidents.
They will rather terminate that article.
Wikipedia deletes all articles
that are related to gang stalking.
When Pope Benedict XVI was elected,
the Wikipedia editors made a page for him,
with a photograph of the villain from Star Wars.
Wikipedia has a lengthy entry on
Jesus H. Christ.
Wikipedia calls it often
humorous,
joking
and
comedic.
They refuse to admit that it’s an anti-Christian mockery.
Wikipedia uses unflattering photographs for
homosexual
persons.
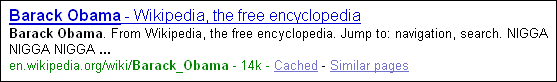
More than thousand pages include the word
nigger,
many in the page title.
Wikipedia denies
global warming,
water fluoridation
and
peak oil.
Wikipedia editors alter the use of the terms
he
or
she
in articles regarding cross-dressing / transsexual figures.
Men attempting to pass as females are called
she
while women attempting to pass as men are called
he.
This usage is absolutely incorrect in both scientific and legal senses.
When NBA Basketball player Jason Collins announced
that he was a homosexual,
his Wikipedia biography was altered to say that he was a
faggot.
When an editor attempted to change the word to
gay
Wikipedia’s anti-vandalism robot changed it back.
There are many complaints of
falsified biographies.
In 2005 the Wikipedia editors attacked prominent journalist John Seigenthaler
for requesting that they remove from his biography
that he was involved in the assassination of JFK.
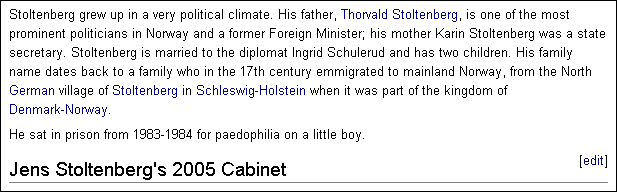
Wikipedia falsely reported that the prime minister of Norway,
Jens Stoltenberg,
was a
pedophile
who had served time in prison.
Wikipedia’s article on
dinosaurs
contains no mention of the strong evidence
that they existed alongside humans.
Wikipedia’s main article on
communism
doesn’t mention any act of genocide in
communist
countries.
Any attempts to edit the page to include this information are deleted.
(They butchered 50 million people.)
Professor Duguid looked up the 17th-century English writer Daniel Defoe.
He found
eight substantial errors in the first paragraph alone,
including Defoe’s date of birth, date of death,
the town where he was born, his father’s occupation,
the reason he changed his name,
and the explanation for his rise to notoriety.
Professor Duguid:
My corrections were undone by people who clearly had little idea what they were talking about almost as quickly as they were made by me.

The 14th century priests burned heretics alive.
This was
logic,
rational,
reasonable
and
scientific.
Psychiatry is just the same.
Poisoning, butchering or electrocuting someone’s brain
is
logic,
rational,
reasonable
and
scientific.
They believe nonsense.
They believe it sincerely.
They become extremely convinced of it.
They strive forever incessantly
to make others agree and conform
to their own ideas and expectations of belief and behavior.
The religious fanatic and the scientific zealot
are simple different versions
of the same nutty phenomenon.
The content of their assertions and beliefs differ,
but the manner in which they function is exactly the same.
In a very real sense
both the 14th century priest and the modern psychiatrist
are nothing more than very dull people,
incapable of calm detached observation of what actually is,
and who chronically believe and assert very stupid ideas
that far too many other people readily accept
without any careful examination or resistance.
And the funniest part is
that generally the scientific folks
attack and claim to be so superior to the religious folks,
in terms of
truth,
reason
and
legitimacy
when they really do exactly the same thing!
They suffer from the same degree of lunacy
as did the religious nuts of the past
which they so correctly criticize and attack.
Do not base your opinion only on
what members of the psychiatric field tell you.
Liquor manufacturers will not tell you
that their products cause liver damage,
that they are the source of numerous automobile related deaths every year,
and encourage you to cease drinking liquor.
In fact, they will involve themselves and you
in endless
rational
discussions and
reasonable
arguments
about
responsible partying,
drinking with control,
designated drivers,
take lots of B vitamins
and so on,
and do everything but suggest the one and only effective and sensible thing.
Simply choose not to drink at all and encourage others to do the same.
Similarly, no psychiatrist will tell you
that psychiatric procedures harm people
and that you should avoid them at all cost.
Even if he or she knew or suspected this,
he or she couldn’t endure the loss of income,
status and authority this would entail.
After all, psychiatry is primarily a business.
It is a money-making venture just like the liquor manufacturers.
It is not a field ultimately concerned with
helping
people and society.
Any honest study of its history and practices makes this abundantly clear.
And again, pay no attention to what they say or claim.
People can and do believe and say anything,
and far too often what they say and believe has nothing at all to do
with
truth
or your best interests.
The mental health community aids in repression
by directly diagnosing
and even institutionalizing against their will
people who claim to be mind control victims.
This is nothing short
of the former Soviet system
of using psychiatry
to discredit and silence dissidents and others.
There really are mentally ill people,
and their illnesses are used as cover lies for torture.
The mental health system should be considered
collaborators in repression,
at least until their diagnostic manuals have entries
for electronic and other mind control,
nonconsensual experimentation,
and trauma and torture sequelae
due to harassment campaigns.
The psychiatric community is used
to enforce belief
in the socially demanded delusion
that the government does not engage
in extrajudicial torture and harassment
of its own citizens
(and the delusion
that the psychiatric community
doesn’t have years of mind control blood on its hands).
The psychiatric and psychological communities
are also used
as tools in the repression and torture.
Sometimes wittingly,
sometimes unwittingly,
mental health workers aid in and help cover up
mind control operations.
First, these communities aid in the repression
by advertising mental illnesses and their symptoms
while ignoring technological means
for inflicting the same symptoms.
They ignore the reality
of government harassment campaigns
and nonconsensual experimentation
on the public.
This lays the groundwork for mind control victims
to be labeled as mentally ill
and dismissed,
or for some half-educated person
to think
that they are helping
by suggesting
that the victim
get psychiatric help.
Deniability is one of the first principles
of covert action,
and inflicting torture
which mimics the symptoms of mental illness
is not especially novel.
The deniability is preserved
by publicizing mental illnesses
while denying mind control technology
and harassment techniques.
Before you start to read websites about gang stalking
you should realize that
disinfo is a very important part of gang stalking.
Victims create websites,
forums, books, videos, MP3’s and so on
to spread their ideas.
Gang stalkers will use the same means
to spread their own distorted version of the truth.
They know government and the press so well
that they can present their material
so if government or the press want to read something about gang stalking
then they will choose something that was made by gang stalkers,
and if they want to invite a speaker,
then they will invite a gang stalker.
Gang stalkers will always try
to suppress the truth about gang stalking.
But, if the word gets out,
then gang stalkers will make it sound as crazy as possible.
Typically,
if you believe that
you are being stalked by several people,
then you will have great difficulty
to say this on TV.
But, if they say something about mind control on TV,
then they invite Magnus Olsson
with his strange stories
about nano implants.
-
Disinfo for the unaware public.
-
Claims that
there is no organized stalking.
-
Claims that
complaints about mind control can be explained as mental illness.
-
Claims that
COINTELPRO has stopped.
-
Claims that
voice to skull can’t transmit an entire sentence into someone’s head.
-
Claims that
gang stalking is an unnotable conspiracy theory of a fringe group.
-
Disinfo for gang stalkers.
-
Claims that
the target has a long criminal record.
-
Claims that
the target is a thief.
-
Claims that
the target is a prostitute.
-
Claims that
the target is a drug user.
-
Claims that
the target is a drug dealer.
-
Claims that
the target is a pedophile.
-
Claims that
electronic harassment is harmless.
-
Claims that
they are doing their community and country a great service.
-
Claims that
what they do is not illegal.
-
Claims that
the victim deserves it.
-
Claims that
the victim ordered the treatment (!).
-
Disinfo for victims.
-
Lies for victims.
-
Claims that gang stalking doesn’t exist.
-
Claims that
gang stalking is an artificial experience that is caused by electronic harassment.
-
Claims that the harassment is not done by the state, the Freemasons and the Mafia.
-
Claims that
the harassment is done by unknown groups.
-
Claims that
the harassment is done by anti-government groups.
-
Claims that
the harassment is done by extremist groups.
-
Claims that
the harassment is done by rogue cops.
-
Claims that
the harassment is done by some private militia.
-
Claims that
the harassment is done by terrorists.
-
Claims that
gang stalkers are not human (devils, aliens, beings from another dimension).
-
Claims that the goal is not total control over every individual.
-
Claims that
the goal is suicide.
-
Claims that
the goal is a rampage.
-
Claims that
the goal is to isolate you.
-
Claims that minimize the role of gang stalkers.
-
Claims that
gang stalkers are unaware of what they do because they are remotely controlled by the technology.
-
Claims that
gang stalkers are unaware how bad it is for the victims.
-
Claims that
gang stalkers are a group of loosely affiliated people.
-
Claims that
only a small number of stalkers are necessary to keep up the harassment of a single victim.
-
Claims that
people are intrinsically good.
-
Claims that
there are also good cops, you should remain polite when you talk to them and you should try to keep them as a friend.
-
Claims that minimize the role of the technology.
-
Claims that
the vivid dreams are not entirely artificial but rather a minor manipulation.
-
Claims that
victims are made sick with poison instead of microwaves.
-
Claims that exotic technology is being used instead of the obvious alternative.
-
Claims that
electronic harassment is done by satellites rather than your neighbors.
-
Claims that
electronic harassment is done by nano-scale implants.
-
Claims that
the stalkers would use through-wall radar rather than miniature cameras.
-
Claims that
the stalkers would use V2K to communicate with each other rather than a miniature earpiece.
-
Claims that
the stalkers would see through your own eyes rather than to use miniature cameras.
-
Claims that
things that grow out of your skin are Morgellons rather than implants.
-
Half-truths for victims.
-
The
75% activist
will try to replace the mind control terms
with terms that are even less known,
for example,
gang stalking
is replaced with
organized stalking,
electronic harassment
is replaced with
electronic assaults,
V2K
is replaced with
V2S.
-
The
50% activist
will cut his information in two parts
and then upload only the first part.
-
The
25% activist
will make a bad choice
to limit the success of his action,
for example,
he chooses a
.info
domain instead of a
.com
domain.
-
The
0% activist
will do something to make his action fail.
For example,
he publishes an ad,
but the text is difficult to read,
or he collects complaints
and he sends them to the wrong authority,
or he encourages others
to complain to the wrong authority.
-
While most disinfo is intentional,
the
donkey activist
will spontaneously repeat someone else’s disinfo.
-
While most disinfo is a personal choice,
the
robot activist
will forcibly repeat silent hypnosis.
-
Some activists will deliberately say half-truths
because they fear
that they will be sent to a mental hospital.
All websites are in alphabetical order.
-
www.AntiChips.com
—
Anti Chips
by Consumers Against Supermarket Privacy Invasion and Numbering
(CASPIAN).
This site is dedicated to
RFIDs.
Many gang stalking victims believe
that they have
RFIDs.
There’s only 1 proven case of illegal implantation with a
RFID.
-
www.GangstalkerDown.com
—
Gangstalker Down Memorial Page
by Cliff Huylebroeck.
Nearly all mass shootings are provoked by gang stalking.
There was one shooter
who claimed that
he was a victim
of gang stalking and electronic harassment.
-
www.implant-victims.com
—
implant victims
by Cliff Huylebroeck.
There are 8 proven cases of illegal implantation.
Gang stalking victims should be aware of implants.
3 of 8 proven victims of illegal implantation
experience gang stalking.
-
 www.MikrowellenTerror.de
—
Mikrowellen Terror
by Dr. Reinhard Munzert.
This medical doctor has made thermal scans of gang stalking victims.
These scans show skin damage caused by energetic weapons.
www.MikrowellenTerror.de
—
Mikrowellen Terror
by Dr. Reinhard Munzert.
This medical doctor has made thermal scans of gang stalking victims.
These scans show skin damage caused by energetic weapons.
-
www.MindJustice.org
—
Mind Justice
by Cheryl Welsh, gang stalking victim and law expert, recognized as a mind control expert by the UNO.
-
 www.totalitaer.de
—
Totalitär
by M. and M. Bott, the authors of
Der Totalitäre Staat.
www.totalitaer.de
—
Totalitär
by M. and M. Bott, the authors of
Der Totalitäre Staat.
-
†
wikiscanner.virgil.gr
—
Wiki scanner.
-
www.aetherometry.com
—
Aetherometry
by Paulo Correa.
He invented a theory about massfree energy.
All his articles on Wikipedia were vandalized and deleted.
-
www.conservapedia.com
—
Conservapedia.
This aims to be a better Wikipedia.
Their articles about homosexuality are pretty conservative.
-
www.TheRegister.co.uk
—
The Register.
It has detailed and carefully written articles.
-
www.wikipedia-is-wrong.com
—
Wikipedia is wrong.
If I remember well,
then most links didn’t work here.
-
www.wikipedia-watch.org
—
Wikipedia watch
by Daniel Brandt.
He’s the most well-known anti-Wikipedia writer.
-
www.WikipediaReview.com
—
Wikipedia review.
This is a forum about Wikipedia.
-
www.WikiTruth.info
—
Wiki truth.
This is the free scandal sheet that anyone can visit.
Registered domain names have a
blue
number.
Bad names have a
red
number.
Good names have a
green
number.
Discussion groups are not in the list.
I never received the confirmation email
while trying to register for such a group,
so I don’t list them.
Torrents are not in the list.
I never succeeded in downloading a torrent,
so I don’t list them.
Some of these websites may be disinfo or even harassment platforms.
Take a look at them and make your own opinion.
If a perp wants to mess with you
then the easiest way is
to pretend that he’s a victim.
Benjamin Simon from Belgium: (His websites tell almost the same.)
Bob S, a lawyer from the USA:
Cliff Huylebroeck from Belgium:
Eleanor White from Canada:
Gregory Morse from the USA:
Dr. Henning Witte from Sweden:
Jewel Krayan, the author of
Electronic torture, electronic rape. Technology and gang stalking at the post office.
Lez
from France
Mark Rich from the USA:
Michael Sweeney from the USA:
Mikael Helin from Sweden:
Miyoko Goto from Germany: (She used the pseudonym Jane Bauer when she applied for asylum in Switzerland.)
Monika Stoces from Belgium:
Paolo Dorigo from Italy:
Peter Mooring from the Netherlands: (His websites tell almost the same.)
Roberto Scaruffi from Italy: (He was almost Doctor of Political Sciences.)
Shawnna Armstrong from the USA:
Unknown:
Youcef Zaouali from Belgium:
There are links to 337 gang stalking sites
on this page.
23 sites have a good name (about 7 %).
156 sites have a registered domain name (about 46 %).
About 1 in 5 victims makes a website.
If the number of aware victims grows
at the same rate
as the number of gang stalking websites,
then we can predict the number of aware victims:
This calculation was based
on the observation
that the number of gang stalking websites
grew with 0.22% per day
during 24 weeks.
The following calculation shows a simulation
of aware victims between 1993 to 2013.
Their number grew with 0.057% per day.
Since June 2013 the awareness grows 4 times
faster than in the past 20 years.
I’m
Bachelor of Informatics.
I made my first website in 1996.
I think that I made 8 websites, 4 blogs and 2 forums.
This is a short list of my experiences
with my own websites.
-
All my websites are in free webspace.
-
All my websites have a registered domain name.
-
All my websites are hosted on
Apache
servers.
-
All my websites were written
by a program
that I wrote in
Scheme,
which is a dialect of
Lisp.
-
Test your website
with several browsers
because it can show up differently.
-
If you make a complex website
and you translate it completely
into several languages,
then it becomes nightmarish to update it.
-
It is tempting
to make
URLs
in
JavaScript.
Such links cannot be checked.
They are not spidered.
I made several websites with
JavaScript.
I always had to remove the scripts.
-
Pages load too slowly
when they have a
Java
applet.
I made several websites with
Java
applets.
I always had to remove the applets.
-
I always had to remove the frames.
When people use a search engine,
they can arrive in a frame.
If you link to the rest of your site in a frame,
then that page will appear inside the frame,
except if you use
target="_parent"
or
target="_top"
.
-
I never embed a
color profile
in a picture.
-
I never use
dither.
-
If your document will be displayed at x %,
and you change the resolution
of your pictures to 72.27 * x %
without resampling (scaling),
then they should appear in
Reader
like in your graphics program at 100%.
I tried that
with several text processors
and PDF writers.
The chance that every picture
will appear correctly
is very small.
These tips can save you much headache.
Use always
Windows
line endings
(carriage return
+
line feed)
for all your text files,
except
.htaccess
files require
UNIX
line endings
(line feed).
carriage return
= 13 (decimal)
= 0D (hexadecimal).
line feed
= 10 (decimal)
= 0A (hexadecimal).
-
Use a link checker.
-
The names should be shorter than 32 characters
so they won’t give trouble
when they are copied to a
Classic Macintosh.
-
All your files should have a different name
even when they are in different folders.
-
Use the shortest extensions
(htm
instead of
html,
jpg
instead of
jpeg
and
tif
instead of
tiff).
-
Place all
HTML
files in the root.
Then there won’t be
../
in your links.
-
On some servers
a style sheet needs to be in the root.
-
Place all media files in a
Media
folder
with subfolders for images,
PDF
and so on.
-
You can avoid many
file not found
errors by installing special files:
-
robots.txt
is a simple file
that tells robots
which files they may look at.
-
favicon.ico
is a small image
that appears next to the
URL
in the location toolbar.
This image may be transparent.
A simple 16x16 icon
can be included like this:
<link href="favicon.ico" type="image/vnd.microsoft.icon" rel="icon">
There are several variants.
You can also include an icon for iPhones.
-
humans.txt
is a simple file
in which you may tell
something about yourself.
-
error
documents.
These files are sent
when an error occurs.
-
Summary:
-
Type your text.
-
Never use the word
though.
Many disinfo artists use this word
to show other perps
that they are a disinfo artist.
It’s a sign of recognition.
-
Use a
spell checker.
-
Use a
grammar checker.
-
Convert the special characters.
-
Paste it in your
HTML
page.
-
Use a
HTML validator.
-
Use a
link checker.
-
Your text and style should say your message clearly.
-
Your
HTML
and style should be correct.
Your spelling and grammar should be correct.
Typing mistakes and grammar mistakes are a downer
that makes people tune you out.
-
Mistakes in tables
(incomplete rows or columns)
can become visible
when someone opens the page in
Word.
Then you can become the object of mockery.
-
Your pages should load quickly.
-
Your pages should use little memory.
-
It should be easy to update your pages.
-
HTML
was designed to
define the contents
of a page.
It was not designed to
define the layout
of a page.
So generally,
the more you care about the layout,
the more trouble you may expect.
-
Verdana
was designed to be the most readable font for websites.
-
Indent your text and balance your tags:
<ol>
<li>
Demo.
</li>
</ol>
-
Convert special characters to character entity references:
©
Convert especially those that are part of the
HTML
syntax:
"
<
>
-
Put values of attributes
always between single or double quotes
even when they are numbers:
border="0"
-
When you link to a
PDF
or to a page on another website
then you should open it
in a new window:
<a href="http://…" target="_blank">text</a>
Otherwise they
leave
your website.
-
Use
smart quotes:
“Hey,” he said, “When I say ‘Go’ you start running.”
-
I use always
GIF,
JPEG
and
PNG.
They have a comment
with a list of my websites.
Sometimes one of my pictures
is copied to another website
which displays also the comment.
This creates a link to my websites.
-
My pages appear faster because every
img
tag has a
width
and
height
attribute.
-
Every
img
tag needs to have an
alt
attribute.
-
I use always lossless compression.
-
I use always
QuickTime 6
compression.
-
JPEG
isn’t really lossless.
Every time you recompress it,
you lose a bit of the quality.
You should always keep the original picture.
-
JPEG2000
is often advertised as lossless
but it is not lossless.
Try it and you will see.
-
PNG
is generally a good choice
for Windows screenshots.
PNG
is like
GIF
but
PNG
has millions of colors while
GIF
has 256 colors.
If you have doubt,
then save your picture
in multiple formats
and then see
which is smaller.
-
If a picture contains
a photograph
then you should use
JPEG,
even if there are large parts
with the same color.
If it really matters that the colors are correct
then you should use
PNG.
For example,
if a button has round corners
and the rest of the rectangle is filled with the page color,
then you should use
PNG.
-
A website with anti-aliased pictures and text
looks more modern.
Modern computers can work with
color management.
The goal is that every picture appears everywhere
with the right colors.
For example,
if a picture has been made by a scanner or camera,
and you want to display or print it,
then you need the
color profile
of the scanner or camera
and the
color profile
of the monitor or printer.
Special software like
ColorSync
will adapt the colors of the picture.
The
color profile
can be embedded in the picture.
-
Too dark pictures
are the most common problem
in digital photography.
-
Before you work with pictures,
you should check the
color management
preferences
of your graphics programs
and the control panel
ColorSync.
Perps like to change these settings
and then your pictures are typically too dark.
These programs come like an affliction,
but they are capable of shredding all your pictures.
-
When you don’t use
color management,
and you open a picture with an embedded
color profile
then it appears with ‘incorrect’ colors.
But, if you save it as a picture without embedded
color profile
then the colors can be automatically converted
to fit the
color profile.
This means that the colors of your picture are ‘correct,’
but possibly not what you wanted,
because it can be different from what you saw on screen.
-
If you convert a picture,
then you should always compare
the result to the original.
-
When you change the
color profile
of your monitor
then this doesn’t change
the colors that you measure on screen.
Color reduction
is changing the bit depth of the picture
from 32 bit to 16, 8, 4, 2 or 1 bit.
Some programs allow you to choose exactly how many colors you want to use.
-
GraphicConverter
can automatically dither during color reduction.
You can disable this in the
Options
menu in the
Colors
item of the
Picture
menu.
-
The
color table
of a picture with indexed colors like
GIF
can be minimized.
This means that pixels with the same color
have the same index,
and every color appears only once
in the color table.
This creates a smaller file.
-
If you change from X colors to Y colors
but you used no more than Y colors,
then your colors remain unchanged.
Otherwise, your colors are changed.
So when you save as a
GIF
then you should compare
the result to the original.
Especially when you reduce to 4 colors,
the colors can be unacceptable.
-
Some servers don’t accept
GIFs
with a particular bit depth.
So if you upload a
GIF
and you get an error,
then it could be the bit depth.
I use the program
GraphicConverter,
which I usually call
GraphicDestructor
or
ColorGrinder.
I pay a bit more attention to this program
because it’s typical of the trouble
that you can get
with graphical programs.
-
It can damage the directory
because it saves temporary files
in the root.
You can prevent this
by choosing a
RAM disk
as the scratch disk.
-
It has many settings,
and some are in unexpected places.
If you are not careful,
then your pictures are destroyed.
-
It can automatically dither the clipboard.
You can disable this in the preferences.
-
It can
optimize
the colors of a
GIF.
This creates indeed smaller files,
but with loss of quality.
-
It has the best scaling.
Use bicubic resampling for anti-aliased pictures.
For pictures with jaggies
(without anti-aliasing)
nearest neighbor resampling
might be better.
-
Use
smooth
fonts.
They use more colors,
but the distance
between the characters will be better.
-
If you double click
on a text layer
then you get a window with options
for adding shadows to text.
-
Learn to align layers.
-
Learn to align layers to a selection.
-
Store your work as a
PSD
with layers.
-
This program has some features from Photoshop.
It allows you to change the gamma.
-
It allows you to type on a path.
-
PDF
has become an important feature of websites.
You should learn to perform
all types of conversions.
-
Acrobat
is a program that can edit
PDF
documents.
-
Acrobat 6
(PDF 1.5)
is the last version
that you can use
without software activation.
-
PDF 1.5
(Reader 6)
and higher can be compressed.
-
There are problems on a
Classic Macintosh
and some versions of
UNIX:
-
PDF 1.4
(Reader 5)
is the highest version
that can be used.
-
Uncompressed documents
of a higher version
can often be viewed.
-
JPEG2000
images cannot be viewed.
-
PDF Split And Merge
allows you to split and merge documents
with embedded subsets of fonts.
This cannot be done by
some versions of
Acrobat.
It can convert between
Reader 3
and
Reader 8.
If you want a compressed file,
then the result has to be
Reader 6
to
Reader 8.
-
Atomic PDF Password Recovery
allows you to remove the security in a snap.
-
If you don’t have a registered version of
Acrobat
then
doPDF
allows you to print to a
PDF 1.5
(Reader 6)
document.
This will convert
JPEG 2000
images to
JPEG.
Of course,
you would like that
websites like
Google
find everything on your website.
-
A website with
simple HTML
can easily be viewed and spidered.
-
It can be copied by
www.archive.org.
They will publish it
between 6 and 24 months after they copied your site.
This is a slow website.
If your
HTML
is really simple,
then it can comfortably be viewed
on this website.

If your website is hosted on an
Apache
server, then you may define
.htaccess
files.
They define how people may access your website.
You can stop people from
displaying your files
on their website.
That would be theft of bandwidth.
Example:
RewriteEngine on
RewriteCond %{HTTP_REFERER} !^http://gangstalkingdemo.com/.*$ [NC]
RewriteCond %{HTTP_REFERER} !^http://gangstalkingdemo.com$ [NC]
RewriteCond %{HTTP_REFERER} !^http://www.gangstalkingdemo.com/.*$ [NC]
RewriteCond %{HTTP_REFERER} !^http://www.gangstalkingdemo.com$ [NC]
RewriteCond %{HTTP_USER_AGENT} !(googlebot|xenu|yahoo) [NC]
RewriteRule .*\.(css|gif|ico|jpg|pdf|png|txt|zip)$ - [F,NC]
ErrorDocument 401 /errors/401.shtml
ErrorDocument 403 /errors/403.shtml
ErrorDocument 404 /errors/404.shtml
ErrorDocument 500 /errors/500.shtml
Options -Indexes
The first 7 instructions mean
that files with the extensions
css,
gif,
ico,
jpg,
pdf,
png,
txt
and
zip
may only be accessed by
HTML
pages on the site
www.gangstalkingdemo.com
and by the robots
googlebot,
xenu,
and
yahoo.
Then you can check your links with
Xenu’s Link Sleuth.
You can also define error documents.
The last line means
that the server may not generate
an index document
if someone types the
URL
of a folder on your website.
You may put a
.htaccess
file in every folder.
The
.htaccess
file of a folder overrides the
.htaccess
file of its super folder.
You can create an unprotected folder
in which you put files
that may be copied.
For example,
you can put here a
PDF
which contains links to your websites.
This file will be copied by websites
which collect
PDF
files.
They display these files on their website.
This creates a link
to your websites.
-
What is your goal?
- Is this a hobby for personal gratification?
-
Is this a hobby for learning
HTML
and picture conversion?
- Do you want to ask attention from anyone?
- Do you want to teach victims?
- Do you want to teach non-victims?
- Do you want to help other victims?
- Do you want to correspond with other victims?
-
Who will read your website?
- Anyone?
- Victims?
- Non-victims?
- People who search this information?
- People who arrive here by accident?
-
How many people can read your website?
- Which language will you use?
- What is the readability of your texts?
- How old are your readers?
-
What is your relation with other websites?
-
Are you going to compete by providing the same type of information?
This website competes with many others.
-
Are you going to complement by providing a different type of information?
My websites
www.GangstalkerDown.com
and
www.implant-victims.com
are good examples.
-
Is it easy to navigate your website?
-
If someone comes to your website
to search information,
then can he find it easily?
- Do you want a few long scrolling pages with a few links?
- Do you want many short pages with many links?
-
How will you build your website?
-
Do you want to write
HTML
in a text editor?
- Do you want to use software?
-
Do you want fast static
Web 1.0
pages
that you type in
HTML
or slow
Web 2.0
pages with many features
that are created dynamically
when someone asks for them?
-
How many people can access your website?
- What is the size of your pages?
- How much bandwidth do you need?
-
How much may it cost?
- What is the yearly fee?
- What is the chance that you will have to upgrade?
- How many years is it going to be online?
-
How much time may it take?
-
How much time will you spend typing
HTML?
- How much time will you spend taking pictures?
- How much time will you spend answering questions from other victims?
-
How will people find your website?
- Advertisement?
-
Search engines?
- What are they going to search?
-
Which chance do you make that they will pick your website from the search engine results?
There are not many people who search information about gang stalking.
There are already hundreds of gang stalking websites.
Where do you want to appear in the list of these websites?
-
Direct links?
- Do you know people who will place a link to your website on their website?
- Which chance do you make that someone will place a link to your website on his website?
Thus far,
the best way of action
was to publish text and images
on a website.
In my opinion,
your own webspace
with a registered domain name
is the best choice.
I have had several blogs and forums
and I really wouldn’t reconsider.
Advantages:
-
They are hosted on a website
with a high page ranking.
-
They have often a calendar
that creates automatic pages
that are indexed by search engines.
-
They are often on top
of search engine results.
Disadvantages:
-
They have terrible names.
gangstalkingwiki.wordpress.com
would have been a bad name for this website.
-
They can be too modern,
so they cannot be viewed
on an old computer.
Blog pages can often not be viewed
on a
Classic Macintosh
because such a computer has a limited memory.
-
They can be difficult to remove.
-
They are not suitable for teaching someone what gang stalking is.
-
A website with dynamic pages
that take some time to load
will discourage readers
to follow the links on your website.
-
Most people won’t publish
links to blogs
on their site.
-
Don’t take it for granted
that large websites like
blogger
and
wordpress
will be online forever.
They might disappear,
but they can also change their name.
For example,
www.uploadingit.com
changed into
www.firefile.io
so you see that it can happen.
So your first impression
will be that your blog is a success,
because its importance is overrated.
But after a while you will be disappointed
because people don’t create links to your blog
so its success will be limited.
If you have a hobby,
for example, you do sports competition,
and you would like
that your fans can follow
your recent activity,
then a blog is OK.
Advantages:
-
They are hosted on a website
with a high page ranking.
-
They create automatic pages
with subforums
and 10 messages per page.
All these pages are indexed by search engines.
They are often on top
of search engine results.
Disadvantages:
-
They can be swarmed by perps,
with only perps posting.
-
They can display ads on top,
at the bottom
and in the middle
of every page.
-
It can cost much time
to patrol the forum.
-
As I could see between 2008 and 2013,
people come to a forum only
if it were created by an organization like
FEDAME
or
FFCHS.
A registered domain name
makes no difference.
The best way to put your website online,
is a registered domain name with free web space.
You make text files with the extension htm.
Then you use FTP to upload.
If you wish, then you can still add
a blog or a forum to such a website.
This is better than a free blog or forum
because there are no ads,
and you are completely in control.
But, this can cost much bandwidth.
They might charge you for it.
When you register a domain name,
then many websites will publish
‘interesting’
data
about your website.
So they create links to your website.
(Sometimes they will propose to remove
‘interesting’
data
like your email address
if you are willing to pay.)
Choose a name that is descriptive
and that contains the word
gang stalking
and that ends with
.com.
A .com is always the best choice.
Examples:
-
If your name is
Liz,
and you’re being stalked in
Springfield
then
www.GangStalkingLizInSpringfield.com
is a good name.
-
If you want to explain gang stalking
then
www.GangStalkingExplained.com
is a good name.
-
If you want to network with other victims in
Florida
then
www.GangStalkingInFlorida.com
is a good name.
Some words will result in a better score in the
Google
results. For example:
- www.EncyclopediaOfGangStalking.com
- www.FreemasonGangStalking.com
- www.GangStalkingBooks.com
- www.GangStalkingBusiness.com
- www.GangStalkingCrimes.com
- www.GangStalkingDeals.com
- www.GangStalkingForSatan.com
- www.GangStalkingForTheDevil.com
- www.GangStalkingIsTheMasons.com
- www.GangStalkingMasons.com
- www.GangStalkingNazis.com
- www.GangStalkingOperations.com
- www.GangStalkingPranks.com
- www.GangStalkingScams.com
- www.GangStalkingShop.com
- www.GangStalkingTerror.com
- www.GangStalkingVideos.com
The best design for a website
is hierarchical.
Visitor statistics have to be interpreted correctly.
-
Many visitors are spiders or robots
(like search engines).
-
Many visitors are referer spam.
They request a file from your website
with an extra line to the request
that contains a link to the website
that they want to promote.
This is recorded in the visitor statistics.
Many websites display these statistics.
Such pages are spidered by search engines.
This makes the promoted website more important.
A website doesn’t make sense
if it has no visitors.
Here are some strategies:
-
Make the website that you want to promote.
Then make a second website.
This uses a script to replace its home page
with the home page of your first website.
Now copy all the websites about gang stalking
that you can find
and add those pages to your second website.
The second website will get a high page ranking,
so your first website will get a high page ranking too.
This worked reasonably well for Eleanor White.
-
A website with a specific message
will attract readers who search
that specific information.
For example,
if you write that you do body building competition
and you experience harassment in this body building world
then this will attract readers who search
information about harassment in the body building world.
Then you could have more readers
than when you write about gang stalking in general
on a small website
with a low ranking
that people never find.
-
Create many websites
with many pages.
Create links to all your websites
on every page.
Write big words like
God, sex, and Nazis on every page
and post large random photographs.
This will fool search engines
and make them believe
that your websites are
“important.”
Then your websites have a good chance
of appearing on top of the search results.
This is the strategy of Benjamin Simon.
It works, although it’s total trash.
-
Create several forums
which mirror their messages.
Every page has a link to all forums.
This technique is called incest.
This works well for
www.bilderberg.org
and
www.politics.be.
-
Advertize your website with
Google
ads.
It works for
www.DataAsylum.com,
although it’s lunatic drivel and disinfo.
-
Visit many websites and forums.
Post a
“What is gang stalking”
article with a link to your website.
This works well for
www.GangStalkingWorld.com.
-
Copy the information from John Finch.
Add a link to your website.
Send it to all email addresses that you can find.
Many people will post this information
on their website.
This creates a link to your website.
-
Referer spam.
-
Say that you are an
“organization.”
Many people will post a link to your website.
This works well for
www.ICAACT.org.
-
The strategy of this website
is that
en.wikipedia.org
is a bad name
that is difficult to type
and difficult to remember
so people type
gang stalking wiki
in their search engine
instead of typing
gang stalking
in
wikipedia.
I copied a few small websites
with much information about HTML:
-
HTML 4 specification
defines all elements and attributes
with examples.
Start with
cover.html.
-
HTML tags reference
has detailed information
about the attributes.
-
htaccess guide
has detailed information
about the
.htaccess
configuration files.
Download
the free HTML help
(ZIP, 672 K).
I made a small website
with all the required functionality:
-
robots.txt,
-
error documents,
-
favicon.ico,
-
style sheets,
-
.htaccess file.
-
The grammar was checked with
Grammarian 2.0.
-
The spelling was checked with
Spell Catcher 8.0.1.
-
The
HTML
was checked with
Alpha 7.4.2.
Download
the free demo website
(ZIP, 84 K).
© 2013 Cliff Huylebroeck





![]()




![]()







![]()
